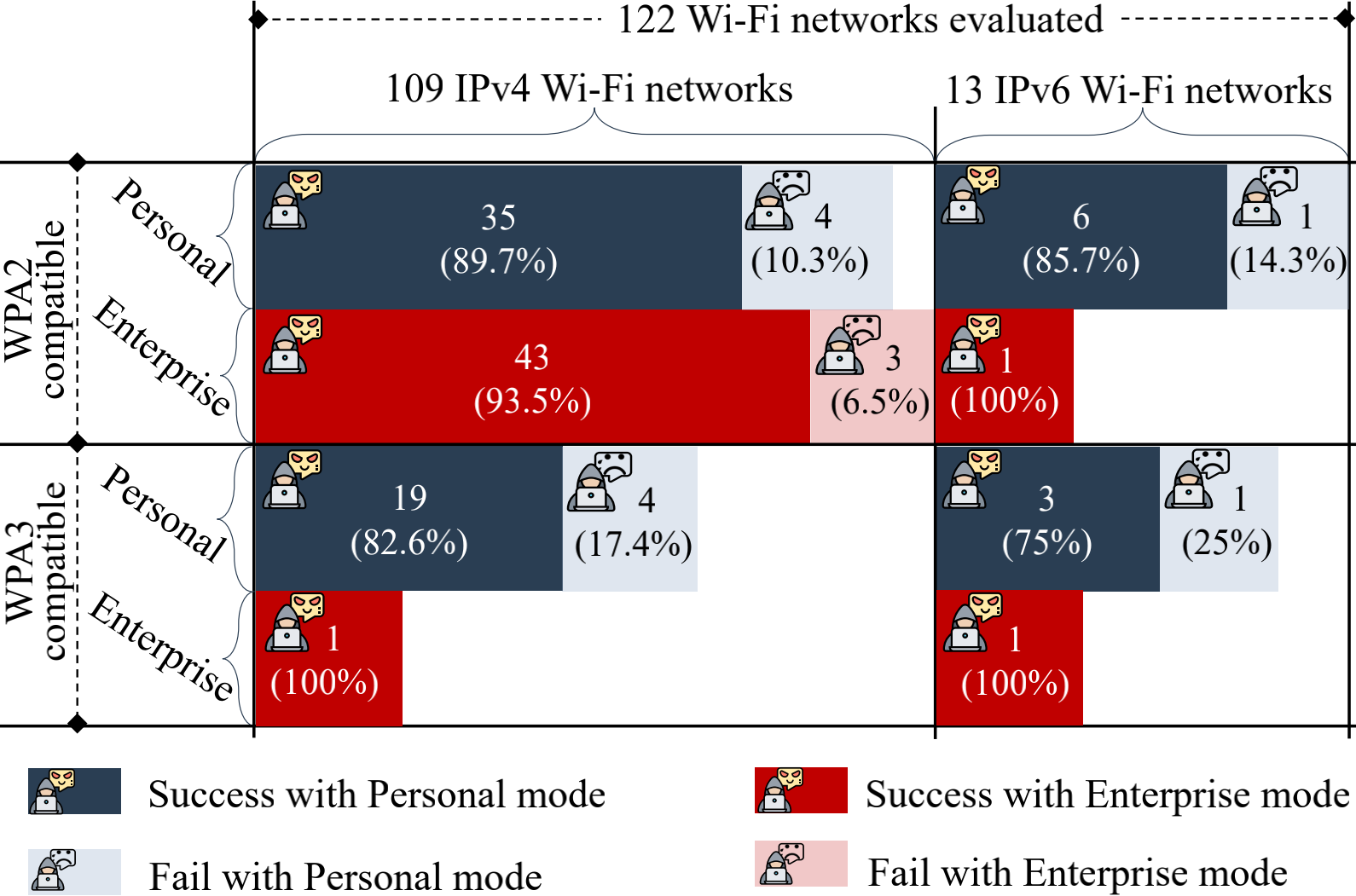
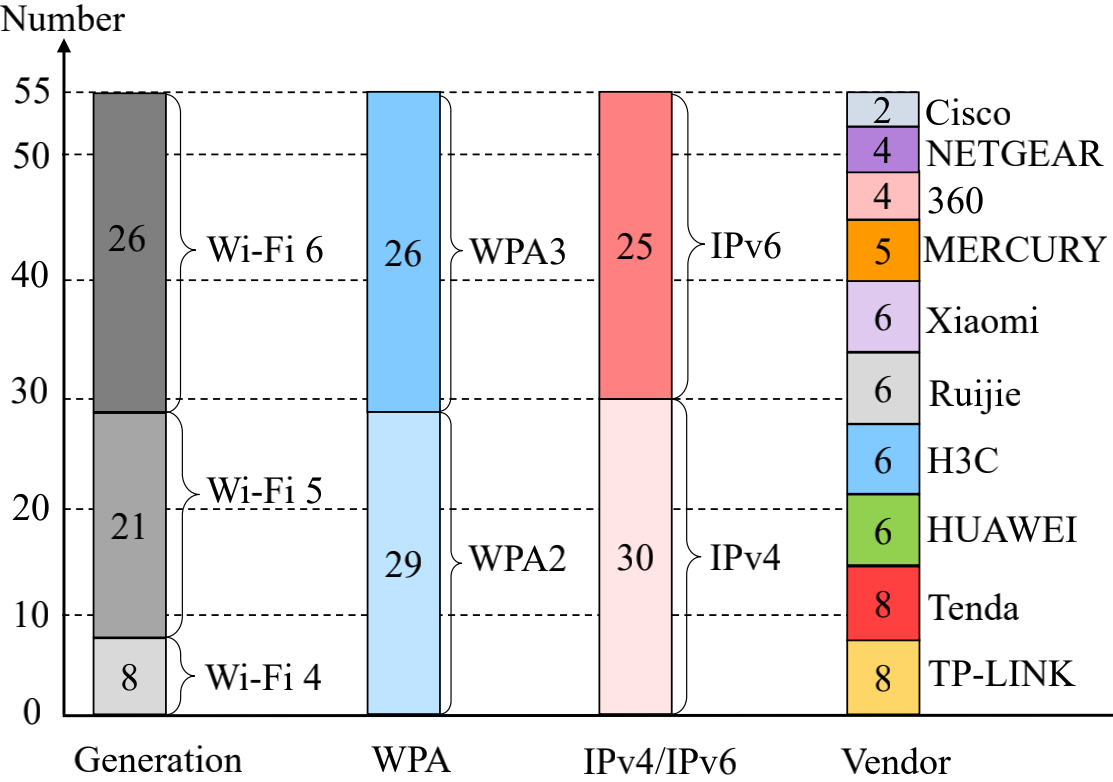
Fig3: Attacks evaluation based on 122 real-world Wi-Fi networks.
Modern Wi-Fi networks are commonly protected by the security mechanisms, e.g., WPA, WPA2 or WPA3, and thus it is difficult for an attacker (a malicious supplicant) to hijack the traffic of other supplicants as a man-in-the-middle (MITM). In traditional Evil Twins attacks, attackers may deploy a bogus wireless access point (AP) to hijack the victim supplicants' traffic (e.g., stealing credentials). In this paper, we uncover a new MITM attack that can evade the security mechanisms in Wi-Fi networks by spoofing the legitimate AP to send a forged ICMP redirect message to a victim supplicant and thus allow attackers to stealthily hijack the traffic from the victim supplicant without deploying any bogus AP. The core idea is to misuse the vulnerability of cross-layer interactions between WPAs and ICMP protocols, totally evading the link layer security mechanisms enforced by WPAs.
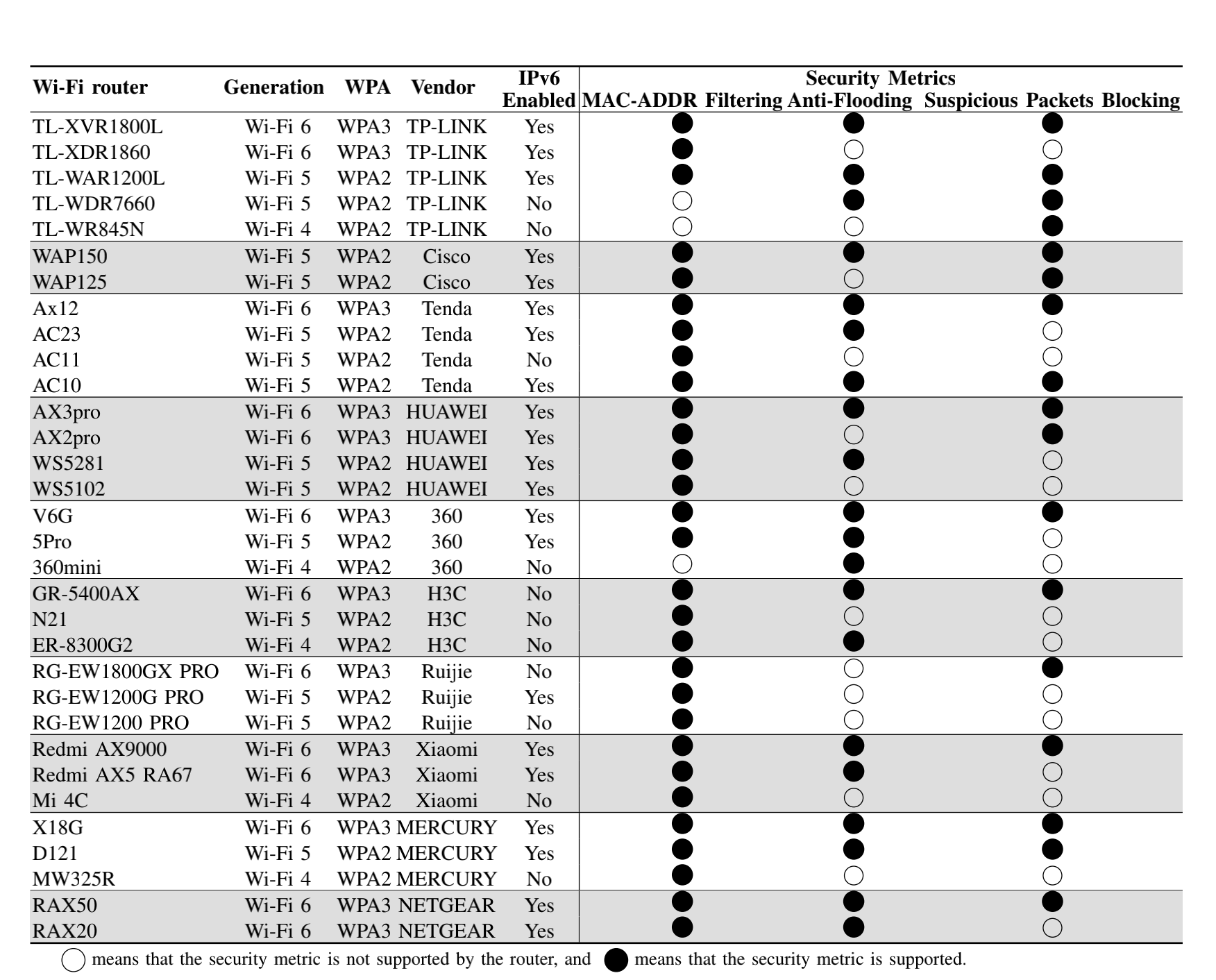
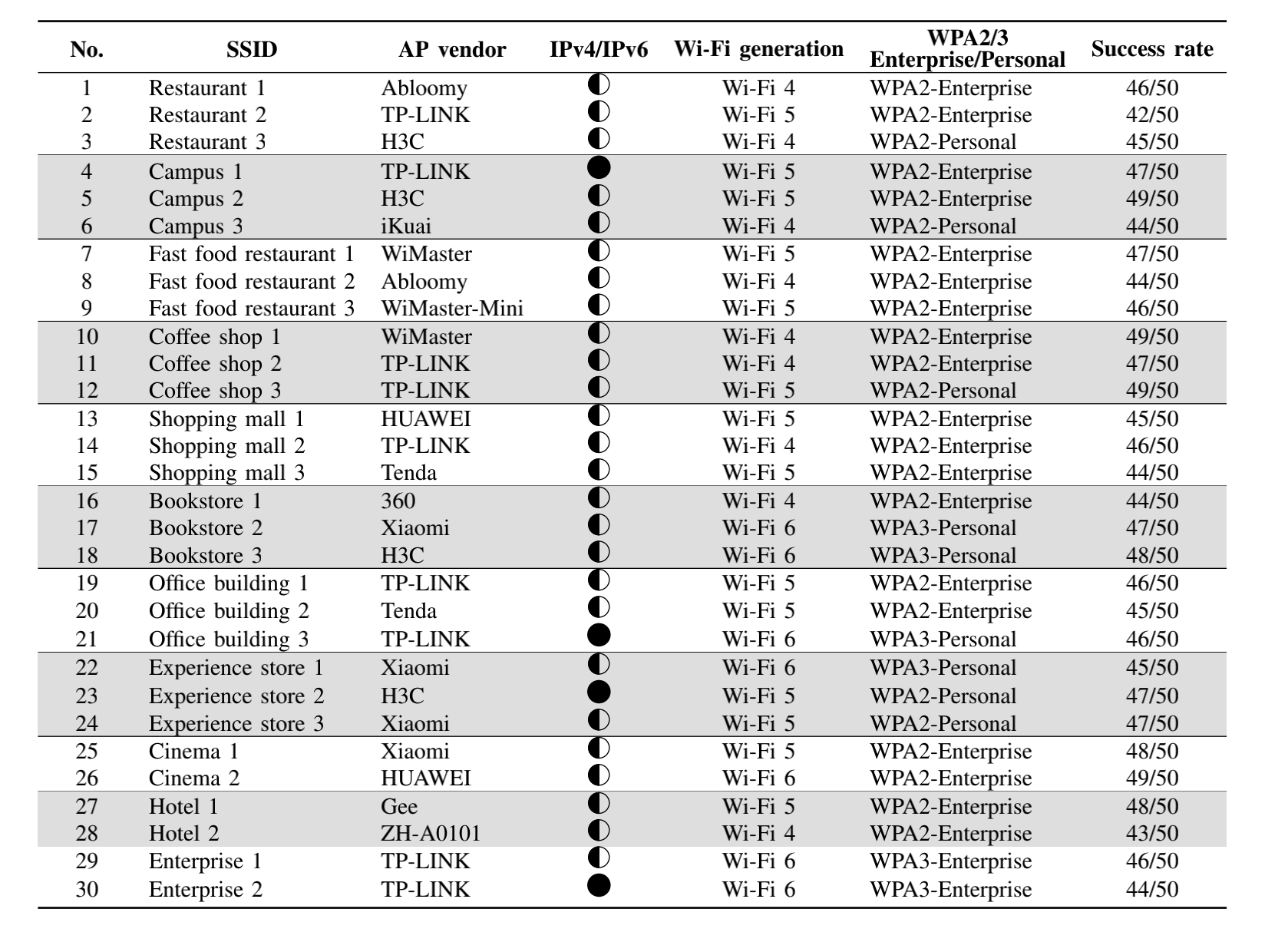
We resolve two requirements to successfully launch our attack. First, when the attacker spoofs the legitimate AP to craft an ICMP redirect message, the legitimate AP cannot recognize and filter out those forged ICMP redirect messages. We uncover a new vulnerability of the Network Processing Units (NPUs) in AP routers that restrict the AP routers from blocking fake ICMP error messages passing through the router. We test 55 popular wireless routers from 10 well-known AP vendors, and none of these routers can block the forged ICMP redirect messages due to this vulnerability. Second, we develop a new method to ensure the forged ICMP redirect message can evade the legitimacy check of the victim supplicant and then poison its routing table. We conduct an extensive measurement study on 122 real-world Wi-Fi networks, covering all prevalent Wi-Fi security modes. The experimental results show that 109 out of the 122 (89%) evaluated Wi-Fi networks are vulnerable to our attack. Besides notifying the vulnerability to the NPU manufacturers and the AP vendors, we develop two countermeasures to throttle the identified attack.
X. Feng, Q. Li, K. Sun, Y. Yang and K. Xu, "Man-in-the-Middle Attacks without Rogue AP: When WPAs Meet ICMP Redirects," in 2023 2023 IEEE Symposium on Security and Privacy (SP) (SP), San Francisco, CA, US, 2023 pp. 694-709.
Figure 1 illustrates the threat model of our man-in-themiddle (MITM) attack. The AP encrypts the network traffic of its supplicants via the security mechanisms developed by the Wi-Fi Alliance. The security mechanisms enforced by the AP can be WPA2 or WPA3. Accordingly, the security mode used by the AP can be WPA2-Personal, WPA2-Enterprise, WPA3-Personal, or WPA3-Enterprise. A victim supplicant (e.g., a mobile phone or a laptop) is attached to a public wireless AP to access remote servers on the Internet. The attacker is a malicious supplicant with no particular demands for the hardware or software. We assume the attacker can access the same AP in both personal mode and enterprise mode before launching our MITM attacks to hijack the traffic sent from the victim supplicant to the remote server.
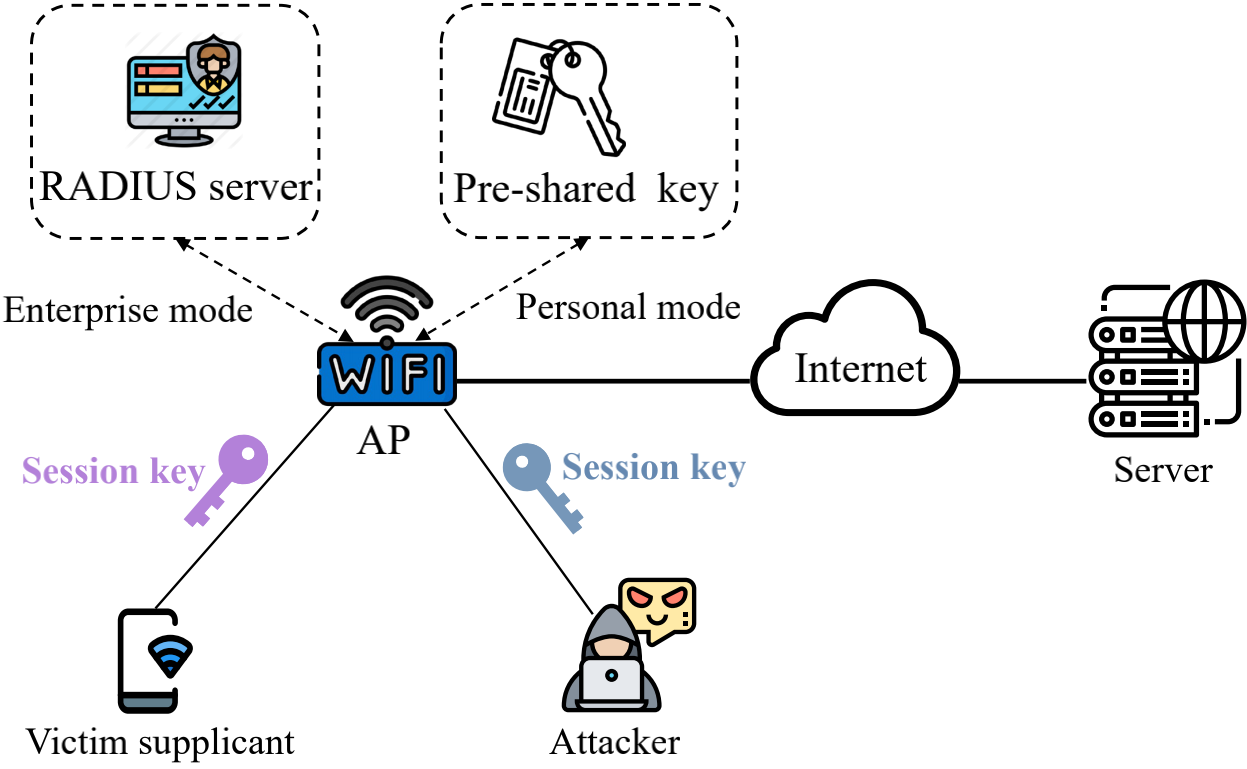
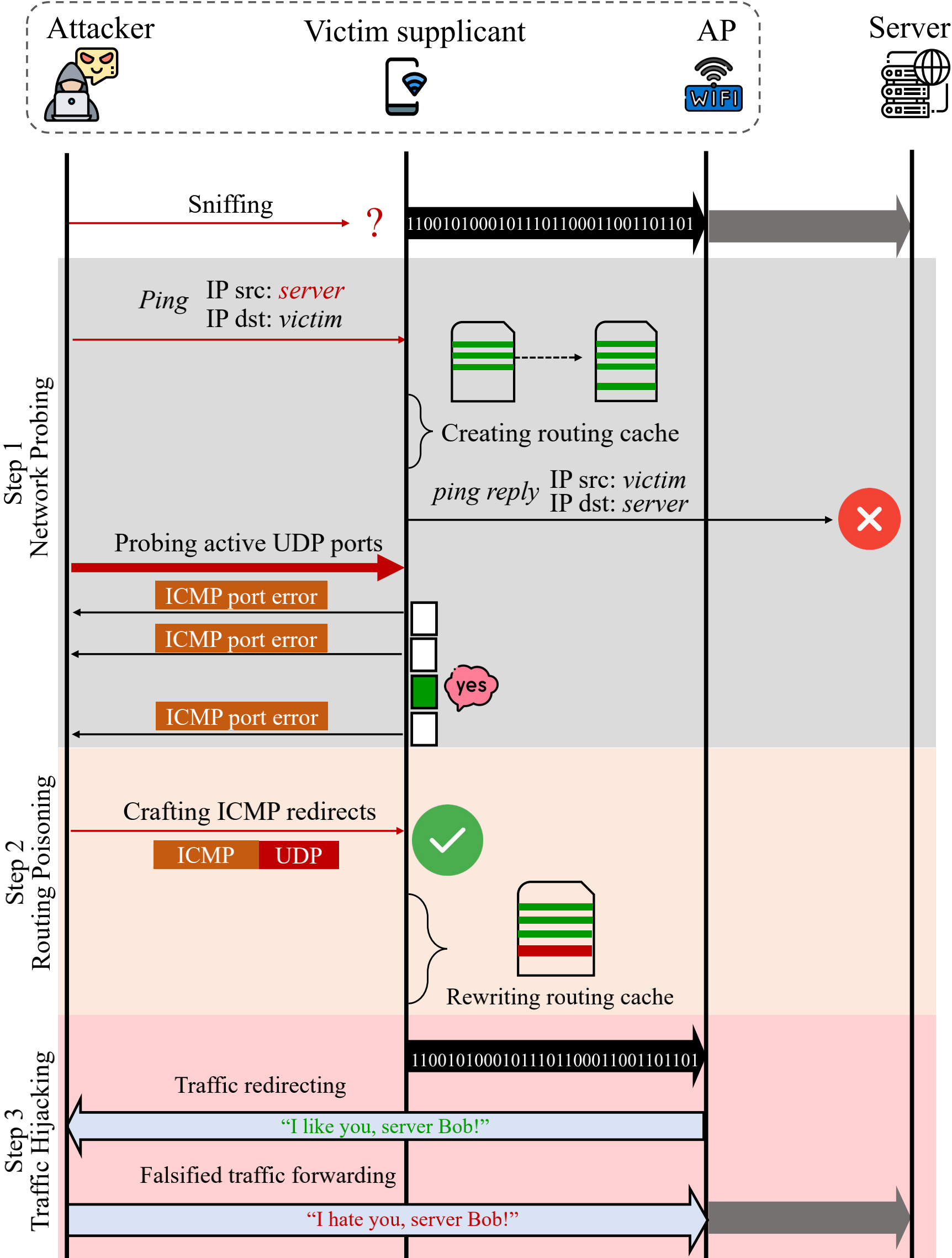
Figure 2 presents the three steps of our attack. At the beginning, the traffic originating from the victim supplicant tothe remote server is sent to the AP and encrypted by a session key between the AP and the victim. The attacker may sniff the encrypted frames, but it cannot decrypt the packets without knowing the session key. In the first step of the attack, by leveraging the ICMP Destination Unreachable Message [14] that is unimpeded in Wi-Fi networks, the attacker focuses on probing the target Wi-Fi network to identify an exploitable UDP port on the victim supplicant. In the second step, the attacker crafts an ICMP redirect message embedded with a fake UDP header (carrying the probed open UDP port) to poison the victim supplicant’s routing. In the third step, the attacker evades WPAs and hijacks the victim supplicant’straffic in plaintext at the link layer. In the following, we elaborate the three steps.
We conduct extensive real-world evaluations to measure the impacts of our attack. We first investigate if vulnerable APs can block crafted ICMP redirect messages issued from an attacker to a victim supplicant. We test 55 popular wireless routers in our lab and find that none of these routers can block forged ICMP redirect messages. Next, we evaluate our attack against the security mechanisms of WPA2 and WPA3 in both IPv4 and IPv6 Wi-Fi networks, respectively. We evaluate 122 real-world Wi-Fi networks and discover that 109 (89%) of them may suffer from our MITM attack.